Frida Hook初次实战 做攻防世界的CTF题,看到有大佬搞Frida的操作,按照大佬做到试了一下
ill-intentions(Native hook) 攻防世界——ill-intentions
frida,frida-server,objection该安装的都安装好
adb连接上机子
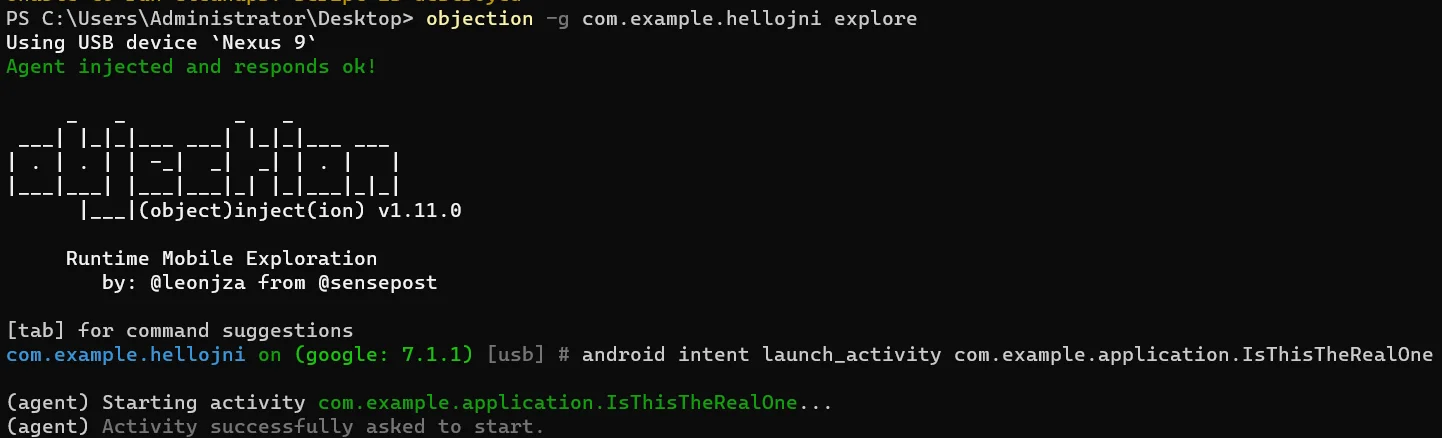
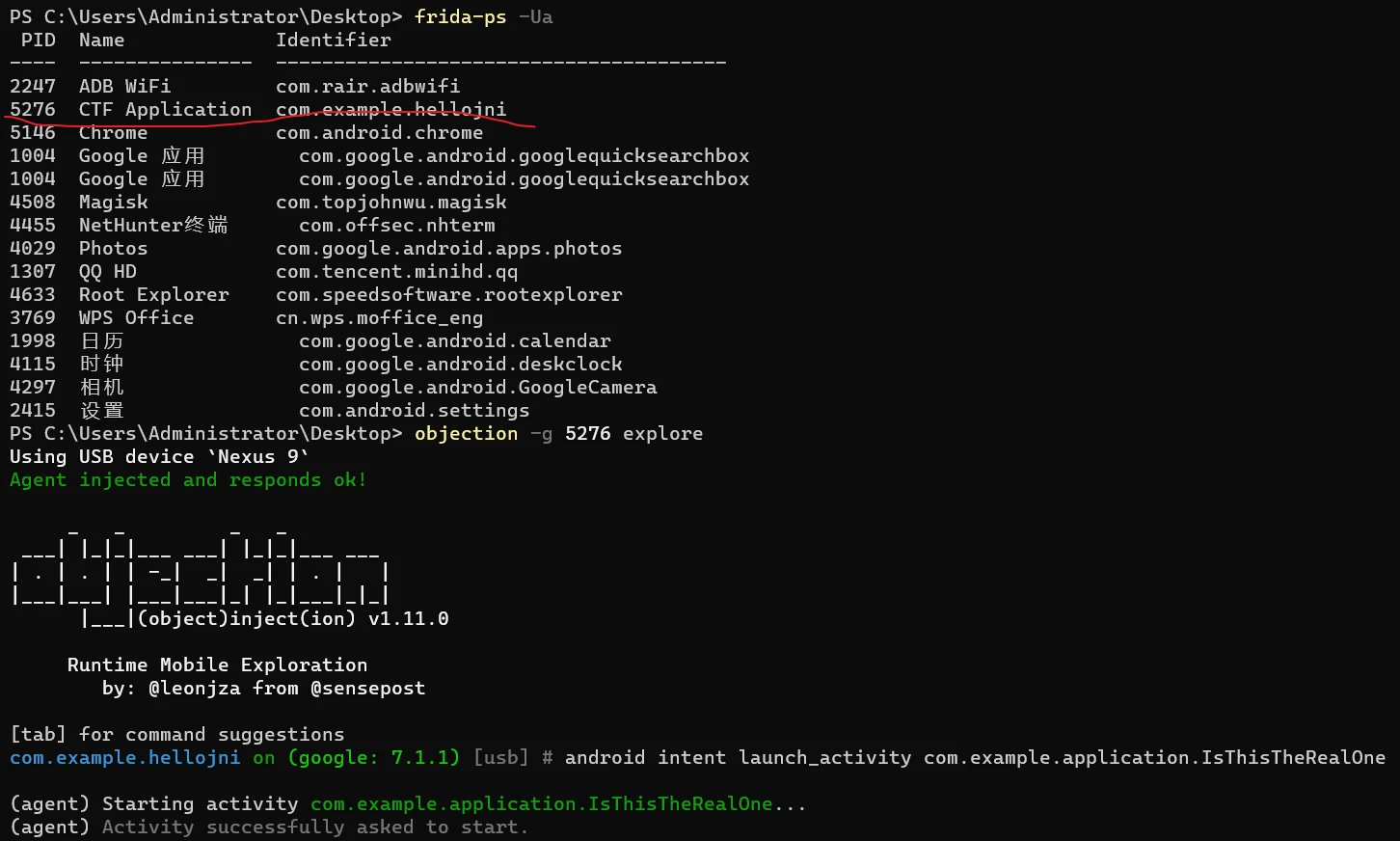
由于没有修改apk包,触发按钮的Intent显示不了,用objection手动开启
1 2 objection -g com.example.hellojni explore android intent launch_activity com.example.application.IsThisTheRealOne
效果如下
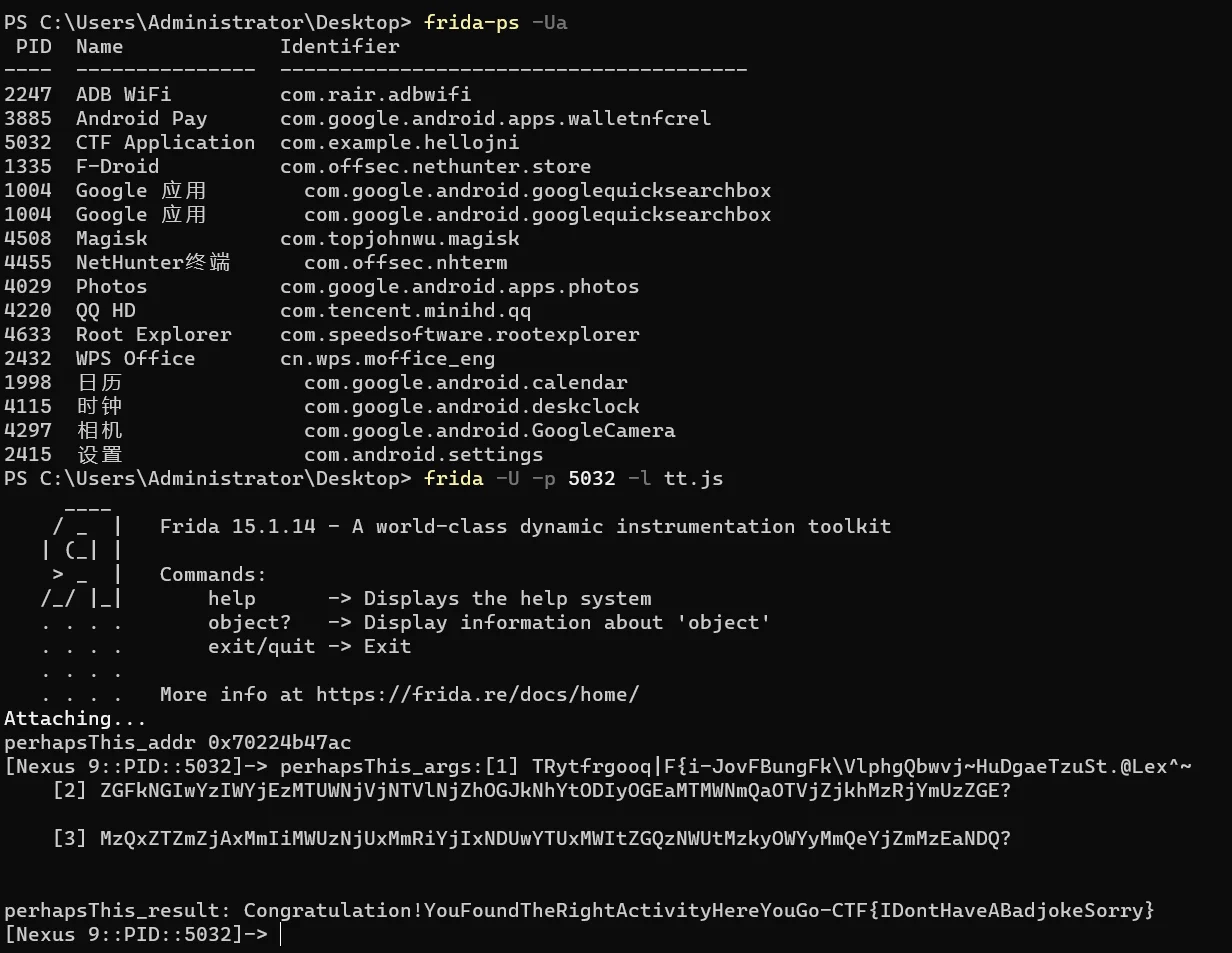
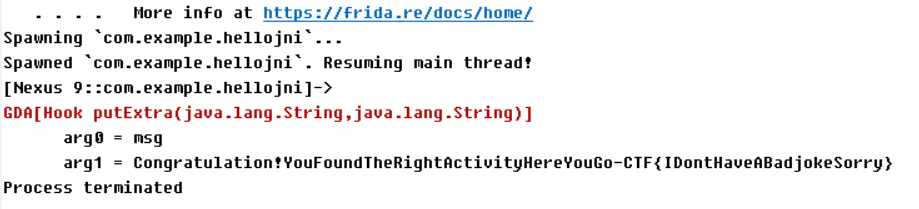
挂上大佬hook Native的脚本
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 function main ( function getjstring (jstr ) { return Java .vm .getEnv ().getStringUtfChars (jstr, null ).readCString (); } Java .perform (function ( var so_addr = Module .findBaseAddress ("libhello-jni.so" ); var perhapsThis_addr = Module .findExportByName ("libhello-jni.so" , "Java_com_example_application_IsThisTheRealOne_perhapsThis" ); console .log ("perhapsThis_addr" , perhapsThis_addr); Interceptor .attach (perhapsThis_addr, { onEnter : function (args ) { console .log ("perhapsThis_args:[1]" , getjstring (args[2 ]), "\n [2]" , getjstring (args[3 ]), "\n [3]" , getjstring (args[4 ]), "\n" ); }, onLeave : function (retval ) { console .log ("perhapsThis_result:" , getjstring (retval)); }, }); Interceptor .attach (Module .findExportByName ("libhello-jni.so" , "Java_com_example_application_ThisIsTheRealOne_orThat" ), { onEnter : function (args ) { console .log ("orThat_args:[1]" , getjstring (args[2 ]), "\n [2]" , getjstring (args[3 ]), "\n [3]" , getjstring (args[4 ]), "\n" ); }, onLeave : function (retval ) { console .log ("orThat_result:" , getjstring (retval)); }, }); Interceptor .attach (Module .findExportByName ("libhello-jni.so" , "Java_com_example_application_DefinitelyNotThisOne_definitelyNotThis" ), { onEnter : function (args ) { console .log ("definitelyNotThis_args:[1]" , getjstring (args[2 ]), "\n [2]" , getjstring (args[3 ]), "\n" ); }, onLeave : function (retval ) { console .log ("definitelyNotThis_result:" , getjstring (retval)); }, }); }); } setImmediate (main);
出flag
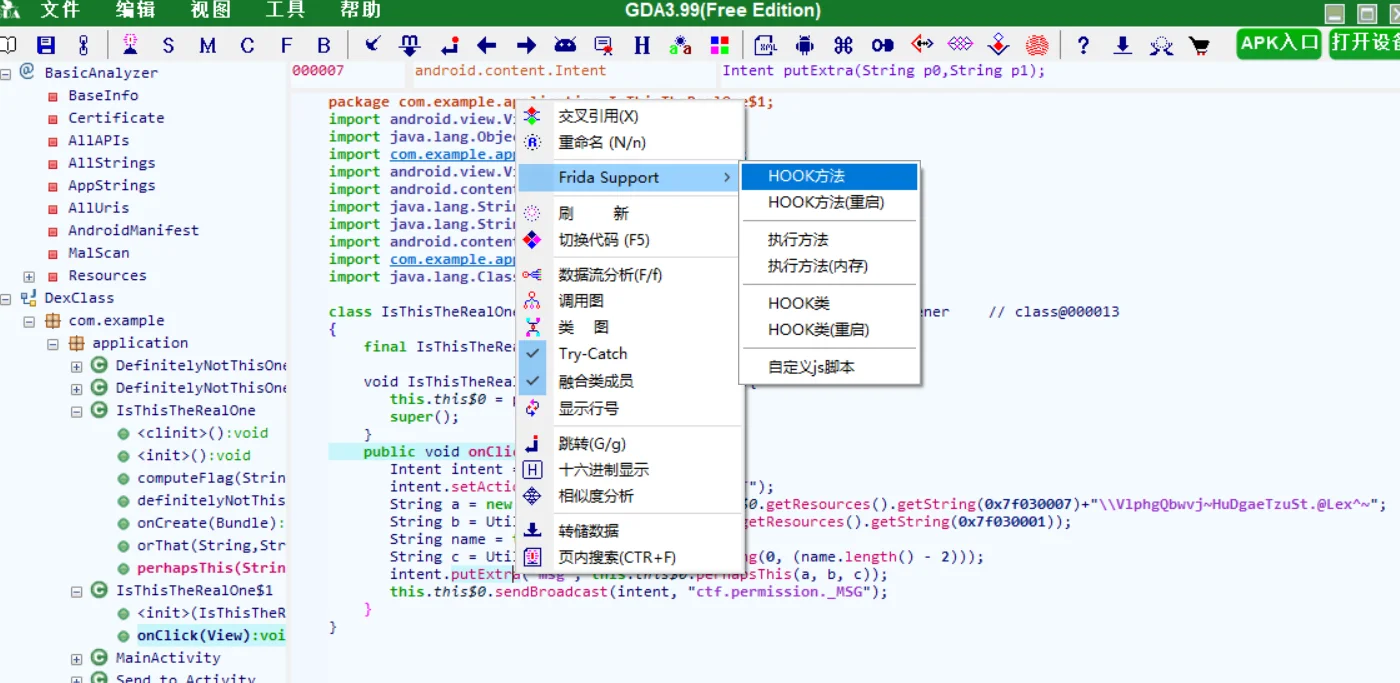
ill-intentions(java hook) GDA 看雪大佬出品的GDA 好用!
还是因为没有修改apk包,触发按钮的Intent显示不了,再次用objection手动开启,找到相对应的进程注入
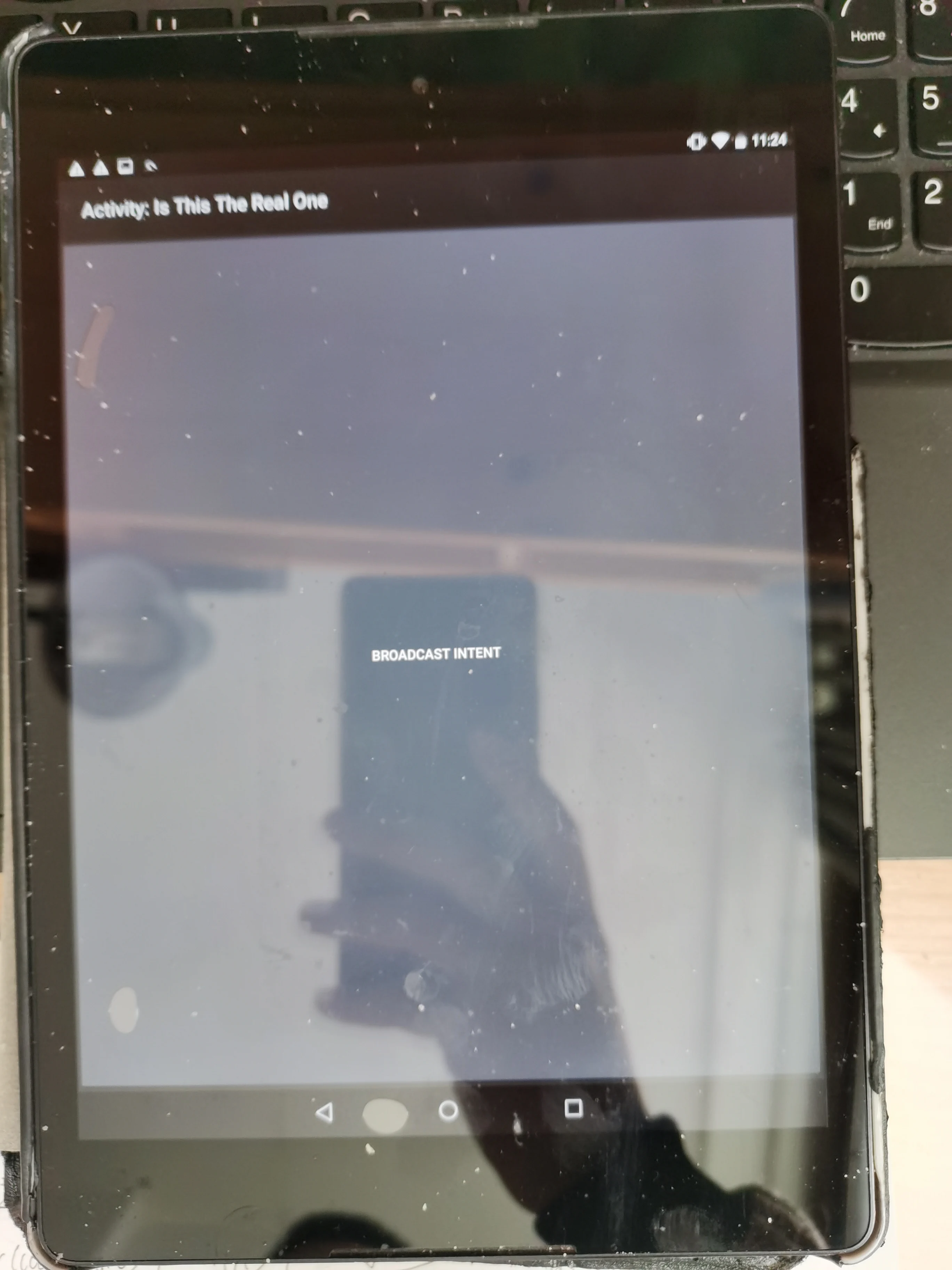
鼠标点击,即可完成操作
按下中间那个BroadcastIntent,就能hook出flag
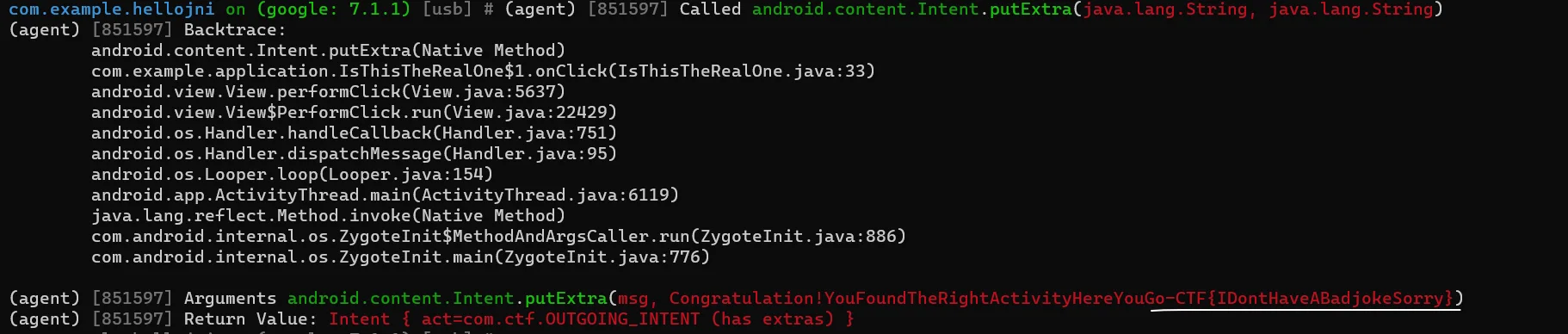
Obejction直接注入 发现GDA那个纯属走弯路,直接Objection注入不就好了
1 2 3 4 5 objection -g com.example.hellojni explore >>CLI中输入 android intent launch_activity com.example.application.IsThisTheRealOne android hooking watch class_method android.content.Intent.putExtra --dump-return --dump-args --dump-backtra ce
遇到一个问题,就是不知道Intent属于什么类,这个是看了GDA里的脚本后才知道的(android.content.Intent),如果想要直接注入的话,需要andriod的开发经验
bilibili-1024-技术对抗赛第6题(2021年) 参考了 https://www.bilibili.com/read/cv13720199/
大佬的脚本少写启动命令,当时折腾一个早上没解决出来
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 function hook_native ( Java .perform (function ( var str0; var arg1; Interceptor .attach (Module .findExportByName ("libc.so" , "__system_property_get" ), { onEnter : function (args ) { str0 = Memory .readCString (args[0 ]); arg1 = args[1 ]; if (str0.indexOf ('ro.product.cpu.abi' )!=-1 ||str0.indexOf ('ro.build.version.release' )!=-1 ){ console .log ('arg0 ' +str0) } }, onLeave : function (retval ) { if (str0.indexOf ('ro.product.cpu.abi' )!=-1 ){ var before = Memory .readCString (arg1); Memory .writeUtf8String (arg1, "x86" ); var after = Memory .readCString (arg1); console .log ('retval:' ,'before' ,before,'after' ,after) }else if (str0.indexOf ('ro.build.version.release' )!=-1 ){ var before = Memory .readCString (arg1); Memory .writeUtf8String (arg1, "9" ); var after = Memory .readCString (arg1); console .log ('retval:' ,'before' ,before,'after' ,after) } } }); }); } setImmediate (hook_native);
方便是真的方便,大佬诚不欺我
结语 Objection好用,降低Frida使用门槛,java层面的hook可以解决很多问题,Native hook老实写frida就行了